Learn Free software with me!
Student projects: PhisSticks BadUSB simulation (video) Cryptocurrency mining dashboard; Analysing software radio with machine learning; student tag; course projects.
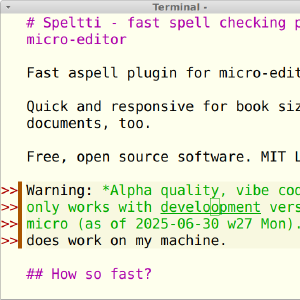
Popular docs: Calendar.txt (HN #1), Install Debian on Virtualbox, Command Line Basics Revisited, Micro editor plugins, Kanasirja offline reference, Cracking passwords with Hashcat, Install WebGoat 8 - Learn Web Pentesting, Crack file password with John, Fuzz URLs to find hidden directories, Translate Offline with AI. Tero's books on Amazon, over 500k sold.
Courses 2024 early autumn: Linux Servers - Linux Palvelimet, Information Security
Courses 2024 late autumn: Penetration Testing - Tunkeutumistestaus, Application Hacking - Sovellusten hakkerointi ja haavoittuvuudet, Configuration Management Systems - Palvelinten Hallinta, Trust to Blockchain
Courses 2025: Network Attacks and Reconnaissance - Verkkoon tunkeutuminen ja tiedustelu, ICT Infrastructure project: SisuCTF Active Directory hacking, Museum3D virtual underwater caves.