 Can you exploit OWASP #1 vulnerability? I wrote a simple vulnerable password recovery app for practicing SQL injections.
Can you exploit OWASP #1 vulnerability? I wrote a simple vulnerable password recovery app for practicing SQL injections.
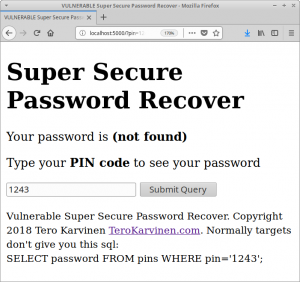
(Vulnerable) Super Secure Password Recover ™ is written with Python 3, Flask and Postgres. You can do bad code even with the best tools.
You can recover your password with your pin. Your pin is “123”. Can you recover the other passwords?
Download the tarball (inject-vulnerable-app-2018.tar.gz)
$ tar xf inject-vulnerable-app-2018.tar.gz
And follow README.
Create and populate the database
$ psql
=> create table pins (id SERIAL PRIMARY KEY, pin VARCHAR(17), password VARCHAR(20));
=> insert into pins(pin, password) values ('11112222333', 'SUPERADMIN%%rootALL');
=> insert into pins(pin, password) values ('123', 'Somedude');
=> insert into pins(pin, password) values ('321', 'foo');
If you want, you can have a look at the data
=> select * from pins;
id | pin | password
----+-------------+---------------------
1 | 11112222333 | SUPERADMIN%%rootALL
2 | 123 | Somedude
3 | 321 | foo
(3 rows)
=> \d pins
Table "public.pins"
Column | Type | Collation | Nullable | Default
----------+-----------------------+-----------+----------+----------------------------------
id | integer | | not null | nextval('pins_id_seq'::regclass)
pin | character varying(17) | | |
password | character varying(20) | | |
Indexes:
"pins_pkey" PRIMARY KEY, btree (id)
Once installed, you can find the vulnerable app on http://localhost:5000
Source Code
#!/usr/bin/python3 # Copyright 2018 Tero Karvinen http://TeroKarvinen.com ######################################### # WARNING: Purposefully VULNERABLE APP! # ######################################### from flask import Flask, render_template, request from flask_sqlalchemy import SQLAlchemy app = Flask(__name__) db = SQLAlchemy(app) @app.route("/") def hello(methods=['POST', 'GET']): pin = request.args.get('pin', '0') sql = "SELECT password FROM pins WHERE pin='"+pin+"';" # WRONG! res=db.session.execute(sql) db.session.commit() row = res.fetchone() if row is None: password="(not found)" else: password=row[0] return render_template('index.html', password=password, pin=pin, sql=sql) if __name__ == "__main__": print("WARNING: Purposefully VULNERABLE APP!") app.config['SQLALCHEMY_DATABASE_URI'] = 'postgresql:///xubuntu' app.run(debug=True, host="0.0.0.0")
Can You Fix It?
Yes, just use the prepared queries provided by the database framework you’re using. Never concatenate user input with SQL.
Careful with Pentesting
As always with pentesting: Be careful. This app is vulnerable, don’t expose it to the Internet. Double check IP addresses. Only test with targets that you know are legal, such as this vulnerable app running on your own computer. Don’t do it if you can’t do it safely. Happy hacking!
Adminstrivia
Updated: added SQL to populate the database.