Cracking Cryptocurrency with Otto
How do you take down a cryptocurrency?

Otto Ebeling visited my penetration testing course. He told us the story of a considerable bug bounty he won and the approach he used.
How do you take down a cryptocurrency?

Otto Ebeling visited my penetration testing course. He told us the story of a considerable bug bounty he won and the approach he used.
My student Miko Hirvelä was publishing his cryptomining profits every minute in 2022.
You can see the revenue (money earned by mining) and profit (after electricity). Investment costs are not included. You can see that times are changing, and it's getting difficult to mine with commodity hardware.
Are you on the plus side? Read how Miko created his dashboard and pull the sources from mikohir/Crypto-Mining-Monitoring.

I published three new plugins for Micro editor this week
You can install them all today.
Published Run plugin for Micro editor.
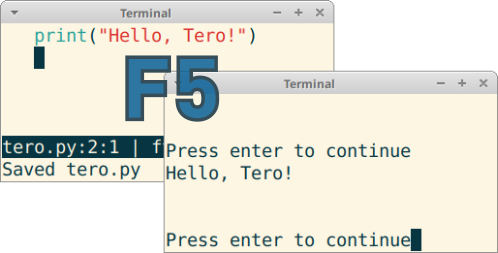
Press F5 to save and run the current file. Supports Go, Go test, Python 3, Lua and executable files.
Press F12 to 'make' the project, F9 to make in background. Also works in subdirectories of your project, thanks to MakeUp(tm) functionality.
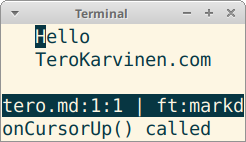
Micro editor plugins can react to user events.
All events that can be bound to keyboard shortcuts, can be used as events in plugins.
function onCursorUp(bp)
-- reacts to CursorUp
end
This post has a table of Micro's every action, onAction function and default keybinding - with explations.
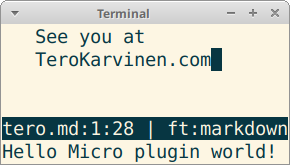
Write your first plugin for Micro editor.
Yours truly (Tero) is the author of micro-jump plugin, and a contributor to micro-lsp. With this beginner friendly tutorial, you can create your first "hello world" plugin.
The plugin we write is very short, just nine lines of code. But here, I explain every little detail of it.

Some versions of NetworkManager produce a lot of log junk. Sometimes, the spurious logs are the main thing jogging the disk.
Keep the useful logs, get rid of the junk. Set CORE:ERR in [logging]. How? Read on...
Access your Python dict with a dot
>>> sn.url
'TeroKarvinen.com'

Using just built-in standard libraries
>>> sn = SimpleNamespace(**d)

Just write what you want (idempotency). Control almost everything with one system (single source of truth). In plain text (infrastructure as code, versionable).
Control 10 computers. Or 100. Or 1000. Or control 2071 computers, like Jussi did on a previous course. Or handle 7 different operating systems and OS versions with a single master, like Matias. Course is in Finnish.
Previous instance got excellent 5.0 / 5 feedback - all respondents gave the best grade 5.
Learn to hack computers to protect your own. In the course, you will break into target computers.
Excellent feedback, 4.9 out of 5.

Could you make a ann app that listens to radio, then summarizes what happened around you when you were away?
My students Dianne, Pauli, Mikko and Juho are going to give it a try. The goal is a proof of concept, not an operator grade box with its own theme song.
Update: MuikkuRF blog, kajami/SDR-project on GitHub.

Learn security fundamentals to understand current trends. Blockchains, TOR network and video conference encryption all stand on these fundamentals.
Excellent 4.9 out of 5 feedback.

Data security course, in English as you asked.
Understand adversarial view on security. Recognize key concepts of security. Be able to safely practice hands-on with security tools.

Learn to manage your own Linux server – in 8 weeks. Remotely, in evenings.
Beginners welcome. Excellent feedback. 4.8 out of 5. Course is in Finnish, 100% remote.
Create your own project with your team.
You'll get the whole 10cr to build your own project.
Previous projects: evil USB keyboard, AI log analysis, physical access control, encrypted communications with free software... What will you build?

Coding in Go, with Micro editor? See function signature (alt-k), definition (alt-d) and references (alt-r).
You can now install language server support in three commands
$ sudo apt-get update
$ sudo apt-get -y install gopls micro golang-go
$ micro --plugin install lsp
Systems don't store original passwords, they store hashes. They look like this "f2477a144dff4f216ab81f2ac3e3207d". Hashing is a one way function, so you can't turn it back to password.
But you can make computer try every word in the dictionary, and tell if one matches. This article shows you how to do this with hashcat.

Normally, Juho 'whois' Jauhiainen is out there to catch computer criminals. Now, he'll tell you, the pentester, how to be invisible.
Whois is the lead investigator at Accenture, a podcast start at Turvakäräjät and a co-founder of HelSec.
Visiting lecture in my penetration testing course 2022-04-04 w13 Monday 09:00 to 10:00.
Install Language Server Protocol (LSP) support for Micro editor
Can you code without the Internet?
What's an <article> and how do I upload a file? What if you could have a copy of Mozilla Developer Network at your fingertips, offline. You can keep your hands on the keyboard, it's TUI with interactive, real time fuzzy search.
Update: Install all dictionaries in one go. New dictionaries: Micro, commands, Arduino...

The final lab for Linux palvelimet course.
Check your English grammar offline, from command line.
Download the latest tlangtool. Free software under the GPL.
It's easy to write web apps with Python Django. To publish your apps on the internet, you must use a real production web server. This tutorial shows you how.
We'll install Python Django 4 using the recommended Apache 2.4 and mod_wsgi. Django is a popular Python web programming framework used by Instagram, National Geographic and Discus.
Build a customer database. Web interface. Multiple users can log in, and edit customer database.
Learn the basics of Django 4, the web framework used by Instagram, National Geographic and Discus.