Tunkeutumistestaus 2025 alkusyksy
Learn to hack computers to protect your own. In the course, you will break into target computers.
Excellent feedback, reached 5.0 out of 5.

Learn to hack computers to protect your own. In the course, you will break into target computers.
Excellent feedback, reached 5.0 out of 5.

Learn to hack computers to protect your own. In the course, you will break into target computers.
Update: We have four great visitors coming, check agenda.
Excellent feedback, reached 5.0 out of 5.

Tips for the first few challenges in Cryptopals.
Learn to break encryption. No math degree required. You do have to be able to code, though.

Review some Python basics to make hacking more convenient. Debugger giving you numbers (84) but you want letters ('T')?
This is about Python basics for supporting hacking. It can support your static analysis with Ghidra, debugging with GDB and ̣getting started with crypto hacking with Cryptopals. I do have many articles on hacking, too.
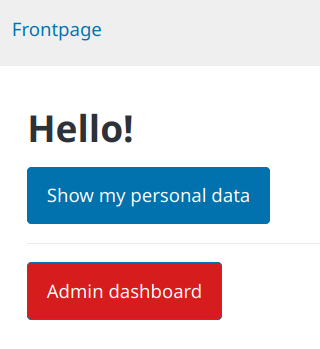 Hack two web apps.
Hack two web apps.
Then fix the vulnerabilites.
Learn to hack computers to protect your own. In the course, you will break into target computers.
Excellent feedback, reached 5.0 out of 5.
 . Update: And latest instance just got 4.9/5 feedback, with 100% NPS.
. Update: And latest instance just got 4.9/5 feedback, with 100% NPS.
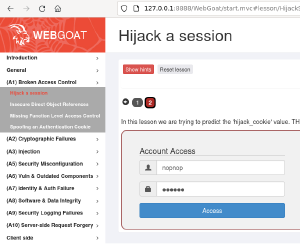
You can learn web penetration testing with Webgoat.
Just download the latest version, install Java with apt-get, set port and run.
Web fuzzers can find unlinked, hidden directories. They can also find vulnerabilities in query parameters.
This article shows you how to install ffufme pratice target and ffuf, the leading web fuzzer.
Web servers often have secret directories, not linked from anywhere.
You could find them by trying different paths manually: /secret, /.svn /admin. This article shows you how fuff can do this to you automatically.
For practice, I coded a target that you can run locally, without Internet. I will also tell you the solution, so you can test your environment. As bonus, there is a challenge target where you can find to solution yourself.
Many file formats support encryption with a password. John the Ripper can crack these passwords with dictionary attack.
This article teaches you to obtain Jumbo version and compile it. Finally, you'll test your environment by cracking a ZIP archive password. A sample password protected ZIP file is provided with this article.
Penetration testing course just finished. Course received overwhelmingly positive feedback.
Feedback average was excellent 4.9 out of 5. So most students gave the best possible feedback grade 5. Read pentest course reviews (in Finnish).
The next Penetration Testing course starts in March 2022. It's fully booked, but as participants are chosen with a test, you can get a place from the queue. Enrollment for the queue opens 2022-01-03 w01 Mon.
An APT (advanced persistent treath) is out to get you.
For hard targets that have done their pentests and audits, someone has to simulate APT attacks to test the defenses.
That someone is Niklas. He runs a red team in F-Secure, and has broken into many networks. And stayed there.
Niklas visits my pentest course tomorrow, w48 Tue 2021-11-30. I have some extra seats, email me to get one.
Learn to hack computers to protect your own.
In the course, you will break into target computers.
Excellent 4.9 out of 5 feedback from previous course.
Update: New visitor: Social Engineering with Riku Juurikko, Senior Security Manager, Elisa.
Update: New visitor: Forensic Analyses with Andrej Bondarenko, CEO, Difseco.
Update: New visitor: How to become invisible with Juho Jauhainen, Lead Incident Response Investigator, Accenture.


Mika protects your payment card purchases.
At work, he has been buying external penetration testing. Now Mika is starting a team doing internal penetration testing for Poplatek (part of Nets). And tomorrow w47 Tue 2021-11-23, he will visit my ethical hacking course and tell us the lessons he has learned.
I have some extra places for those outside my course. The presentation is online and in Finnish.
Learn to hack computers to protect your own.
Course is finished, feedback was 4.9 excellent. Thanks! Next course is Pentest 2022 spring.
In the course, you will break into target computers. Excellent feedback from 4.8 to 5.0 out of 5.
Only one seat left! Advanced course, I can usually get places to most of those who know the prerequisites well.Can't take more participants here. Next enrollment opens 2021-11-29 w48 Mon 08:00. The next course instance starts on 2022 w13.
Update: New visitor: Niklas Särökaari, F-Secure.
Update: New visitor: Mika Rautio, Senior Software Architect, Poplatek.


Don't connect that USB stick you found! Hostile USB can take over your computer, install malware and keyloggers.
My students are developing USB attacks and defences. They have built a cheap and customizable hostile USB device on DigiSpark development board.
Read on to see how to build a hostile USB device similar to "Rubber Ducky" or "BadUSB". And how to defend against this attack.
Learn to hack computers to protect your own. In the course, you will break into target computers. Excellent 5.0 out of 5 feedback (every participant gave feedback, every feedback was 5/5).
Course is in late autumn 2020. Teaching is in Finnish.

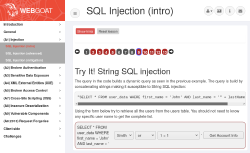
WebGoat is a beginner friendly practice target for web penetration testing.
In this article, I'll install WebGoat 8 on Kali and Ubuntu using Java.
Update: Top feedback: 5.0 / 5. Yes, every participant gave feedback, and each feedback was the best grade 5. Thank you!
Learn to hack computers to protect your own. In the course, you will break into target computers. Previous instance had excellent 4.9 out of 5 feedback.
Course is in late spring 2020. Teaching is in Finnish. Enroll now in Peppi: Tunkeutumistestaus ict4tn027-3003.
