student

Create your own project with your team. You'll get the whole 10 cr to build your own project.
Previous course 2025 projects completed: SisuCTF Active Directory capture-the-flag competition for hackers. Museum3D - a game for museum, using real 3D maps created by divers. JES plant watering and monitoring. RoomTracr room occupancy tracker. ÄJAK key reminder. AIMLOps MLOps platform improvements.

SisuCTF Hack. Defend. Conquer. Active Directory capture-the-flag competition for hackers.
Museum3D - Dive inside water filled cave. A 3D game for museum, using real 3D maps created by divers.
JES Automated Plant Watering and Monitoring System. RoomTracr Track room occupancy and environmental conditions. ÄJAK Never forget your keys. AIMLOps Improvements to MLOps platform.
2025 projects completed.
My student Miko Hirvelä was publishing his cryptomining profits every minute in 2022.
You can see the revenue (money earned by mining) and profit (after electricity). Investment costs are not included. You can see that times are changing, and it's getting difficult to mine with commodity hardware.
Are you on the plus side? Read how Miko created his dashboard and pull the sources from mikohir/Crypto-Mining-Monitoring.

Could you make a ann app that listens to radio, then summarizes what happened around you when you were away?
My students Dianne, Pauli, Mikko and Juho are going to give it a try. The goal is a proof of concept, not an operator grade box with its own theme song.
Update: MuikkuRF blog, kajami/SDR-project on GitHub.


My students Niko Heiskanen and SharkTal wrote a book shop, hlgbooks.com
Buy Niko's booklet "Paypal Integration", 1 EUR. The shop is more beta than the greek letter β, but you can buy from their website if you register first.
And yes, you can have the source code.

Infrastructure projects are completed. Projects varied from evil USB devices to mapping radio signals.
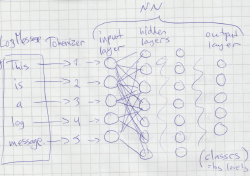 Can artificial intelligence pick suspicious log entries? My students Tuomo Kuure and Joni Hakala are training a model for that.
Can artificial intelligence pick suspicious log entries? My students Tuomo Kuure and Joni Hakala are training a model for that.
They use ELK to collect logs from multiple computers to an ElasticSearch NoSQL database. These log entries are then analysed with their own model using Python Tensorflow in a Docker container with GPU support.






 Can artificial intelligence pick suspicious log entries? My students Tuomo Kuure and Joni Hakala are training a model for that.
Can artificial intelligence pick suspicious log entries? My students Tuomo Kuure and Joni Hakala are training a model for that.